On July 13, 2024, Thomas Matthew Crooks bought 50 rounds of ammunition on his way to Butler, Pennsylvania, drove to former President Donald Trump’s campaign rally at the Butler Farm Show grounds, and climbed onto the roof of the American Glass Research (AGR) building less than 200 yards away from where the former President was speaking, where at 6:11 pm, he fired eight rounds from an AR-15 semiautomatic rifle, killing one person and injuring three others including the former president. That day, he was able to fly a drone 200 yards from the site, use a rangefinder capable of gauging the distance to the former president less than an hour before he began speaking, and bring two explosive devices within proximity of the site of the rally. The United States Secret Service’s (USSS’) planning, communications, intelligence sharing, and related security failures in advance of and during July 13 directly contributed to Crooks’ ability to carry out the assassination attempt and kill and injure people in Butler, PA that day.
On July 30, 2024, Ronald L. Rowe, Jr., the Acting Director of the USSS, testified in a joint hearing before the Senate Homeland Security and Governmental Affairs Committee (HSGAC) and Judiciary Committee that the attempted assassination “was a failure on multiple levels.” Acting Director Rowe testified before the Committees that he has since initiated several reforms to address clear deficiencies in how USSS provides security for its protectees. During the July 30 hearing, Acting Director Rowe acknowledged USSS responsibility for protecting former President Trump. In a series of transcribed interviews conducted by HSGAC and the Permanent Subcommittee on Investigations, key USSS personnel responsible for planning, coordinating, communicating, and securing the Butler, PA rally on July 13, declined to acknowledge individual areas of responsibility for planning or security as having contributed to the failure to prevent the shooting that day, even when as an agency, the USSS has acknowledged ultimate responsibility for the failure to prevent the former president of the United States from being shot.
…
KEY FAILURES
1. USSS failed to clearly define responsibilities for planning and security at the July 13 rally.
USSS personnel responsible for planning in advance of the July 13 rally denied that they were individually responsible for planning or security failures and deflected blame.
USSS Advance Agents told the Committee that planning and security decisions were made jointly, with no specific individual responsible for approval.
2. USSS failed to ensure the AGR Building was effectively covered.
USSS identified the AGR building as a concern due to the line-of-sight from the roof to the stage, but did not take steps to ensure sufficient security measures were in place.
USSS knew that local snipers planned to set up inside the AGR building and USSS did not express objections or concerns about that placement.
USSS personnel, including the USSS Counter Sniper Team Leader, did not enter the AGR building or go on the roof prior to the shooting.
One USSS Counter Sniper team, whose responsibility included scanning the area around the AGR building for threats, had an obstructed view of the AGR roof.
3. USSS failed to effectively coordinate with state and local law enforcement.
USSS did not give state or local partners specific instructions for covering the AGR building, including the positioning of local snipers.
USSS did not adequately consider state and local law enforcement operational plans.
Communications at the July 13 rally were siloed and USSS did not ensure it could share information with local law enforcement partners in real time.
4. USSS failed to provide resources for the July 13 rally that could have enhanced security.
USSS denied specific requests for additional Counter Unmanned Aircraft Systems (C-UAS) capabilities and a Counter Assault Team liaison.
A USSS Counter Surveillance Unit – which could have helped patrol the outer perimeter that included the AGR building – was not requested by USSS Advance Agents.
5. USSS failed to communicate information about the suspicious person to key personnel, and failed to take action to ensure the safety of former President Trump.
At approximately 5:45 pm, USSS personnel were notified that local law enforcement observed a suspicious person with a rangefinder near the AGR building. By 5:52pm, at least eight USSS personnel had been informed.
Approximately two minutes before shots were fired, the USSS Security Room, located on the rally grounds, was told that there was an individual on the roof of the AGR building.
Shortly before shots were fired, a USSS Counter Sniper observed local officers running towards the AGR building with guns drawn.
…
…
…
…
The post U.S. Senate Homeland Security Committee Interim Report on July 13th, 2024 Trump Assassination Attempt first appeared on Public Intelligence.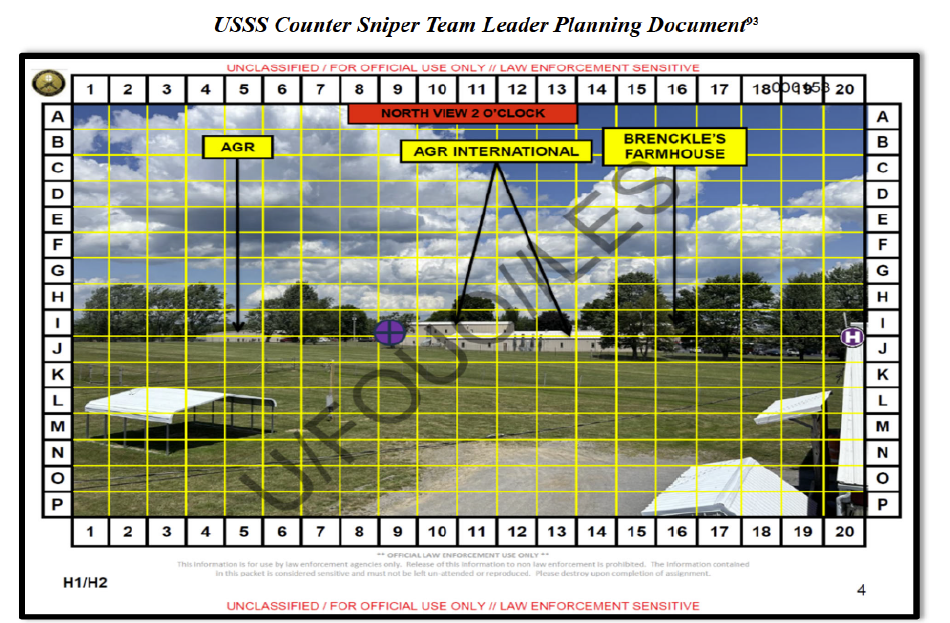










 (U) Using fraudulent license plates, credentials, driver’s licenses, identification cards, or badges from fictitious republics or indigenous groups
(U) Using fraudulent license plates, credentials, driver’s licenses, identification cards, or badges from fictitious republics or indigenous groups , to send an alert as the subject reaches the West Building.
, to send an alert as the subject reaches the West Building.